Penetration testing, commonly referred to as pen testing, is a vital aspect of cybersecurity assessments that involves simulating cyber attacks on systems, networks, or applications to identify vulnerabilities. The primary goal of penetration testing is to uncover weaknesses before malicious actors can exploit them. With the increasing sophistication of cyber threats, effective penetration testing has become essential for safeguarding sensitive data and maintaining the integrity of IT infrastructures.
Types of Penetration Testing
Penetration testing can be categorized into various types based on the scope and approach employed. Understanding these types is crucial for implementing effective security measures that align with an organization’s risk management strategy.
Testing by Access Level
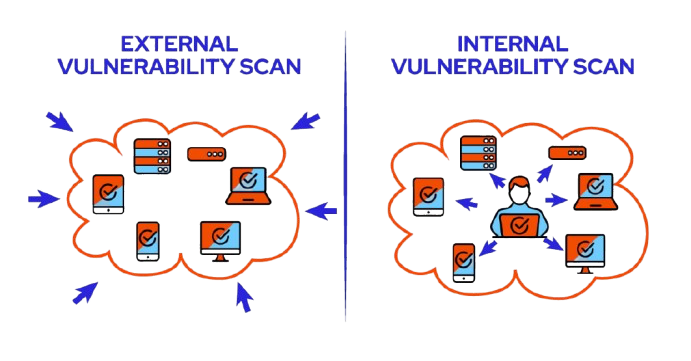
External Penetration Testing
External penetration testing focuses on assessing the security posture of systems exposed to the internet. This type of testing simulates attacks from an outside threat actor's perspective, aiming to identify vulnerabilities in firewalls, web applications, and other publicly accessible resources. By employing external penetration testing, organizations can discover weaknesses that could be exploited by cybercriminals, leading to unauthorized access or data breaches. For instance, an external test might reveal misconfigurations in public-facing applications that could be leveraged to gain access to sensitive internal resources.
In a separate article, we will reveal more details on how A42.tech does this.
Internal Penetration Testing
In contrast, internal penetration testing evaluates security from within the organization. This testing simulates an attack from an insider, such as an employee or contractor, who may have legitimate access to certain systems. Internal penetration testing is critical for identifying vulnerabilities that could be exploited by individuals with malicious intent, whether they are current employees or external attackers who have gained access to the network. For example, internal tests can reveal weaknesses in employee access controls or poorly secured internal applications.
Testing by Attack Methods
Black Box Testing
Black box testing is a methodology where the tester has no prior knowledge of the system's architecture or source code. This approach simulates the perspective of an external attacker, focusing solely on input and output. Black box testing is valuable for assessing how well the system defends against attacks without any inside information. This method helps in understanding how an attacker would interact with the system, often leading to the discovery of vulnerabilities that might be overlooked during internal testing.
Grey Box Testing
Grey box testing combines elements of both black and white box testing. In this approach, the tester has partial knowledge of the system, such as access to user documentation or architecture diagrams. Grey box testing allows for a more targeted assessment, focusing on critical areas while still simulating external threats. This method is particularly useful for identifying vulnerabilities that require knowledge of the system's internal workings while still evaluating how an outsider might exploit them.
White Box Testing
White box testing provides the tester with full access to the system's architecture, source code, and configuration. This method is typically used for security audits and is beneficial for identifying vulnerabilities at a granular level. White box testing can reveal weaknesses that may not be apparent through other testing methods. By analyzing the code and architecture, security professionals can identify logical flaws and potential exploits that could be leveraged by attackers.
Options for Conducting Penetration Testing
Organizations have several options when it comes to conducting penetration testing. These include using internal security teams, outsourcing to specialized firms, or utilizing automated tools.
Internal Security Teams
Many organizations maintain in-house security teams capable of conducting penetration tests. This option allows for greater control over the testing process and immediate access to organizational knowledge. Internal teams can develop an understanding of the organization’s unique risks and can tailor tests to address specific concerns.
Outsourcing
Outsourcing penetration testing to specialized services can provide access to a broader range of expertise and resources. External vendors often have experience with various security assessments and can offer an objective viewpoint. This option is particularly advantageous for organizations lacking the necessary resources or expertise in-house.
Automated Tools
Automated penetration testing tools have gained traction for their ability to improve the testing process. Metasploit serves as an example of such a tool, providing a range of security testing features that allow security professionals to perform tests more efficiently. It can quickly identify vulnerabilities, which can be beneficial for organizations with limited resources. Additionally, tools like Metasploit are often integrated into Kali Linux, a popular operating system specifically designed for penetration testing and security assessments. However, it's important to recognize that automated tools should be used to complement manual testing efforts, as they may overlook complex vulnerabilities that require human analysis.
Built-in Tools for Testing
Several standard security tools are widely used in penetration testing, notably Kali Linux, the Metasploit framework, and others. These tools are essential for conducting effective security testing.
✅ Advantages of Built-in Tools
Quick Access to Essential Tools
Kali Linux provides a suite of pre-installed security testing tools, making it easy for professionals to get started. This accessibility allows teams to begin testing immediately without extensive setup.
Free Solutions
Many tools available on Kali Linux and the Metasploit framework are open-source, allowing organizations to perform security assessments without incurring significant costs. This can be particularly beneficial for smaller organizations or startups with limited budgets.
Ease of Installation and Configuration
Both Kali Linux and Metasploit are designed for simplicity, enabling security professionals to set up testing environments quickly. The user-friendly interfaces allow even those with less experience to navigate the tools effectively.
🚫 Challenges of Built-in Tools
Technical Expertise Required
Despite their accessibility, effective use of these tools requires a certain level of technical expertise. Organizations lacking skilled personnel may struggle to maximize their potential. Proper training and knowledge are essential for accurately interpreting the results of automated scans.
Limited Capabilities Compared to Paid Solutions
While free tools are effective, they may not offer the same depth and features as paid penetration testing solutions, potentially limiting the scope of assessments. Organizations looking for comprehensive testing may find that paid solutions provide more robust features and support.
Plugins and Applications for Automated Testing
In addition to built-in tools, various third-party applications can enhance penetration testing capabilities. Notable examples include Burp Suite and OWASP ZAP.
Burp Suite
Burp Suite is a powerful web application security testing tool that allows testers to identify vulnerabilities in web applications through various methods, including automated scans and manual testing. It provides a comprehensive suite of tools for web vulnerability scanning and is widely used by penetration testers.

OWASP ZAP
The OWASP Zed Attack Proxy (ZAP) is another widely used tool for finding vulnerabilities in web applications. It is particularly valuable for developers and security professionals looking to implement security testing into their development processes. ZAP offers automated scanners as well as various tools to help find security vulnerabilities.

Utilizing Professional BI Tools for Security Reporting
Integrating penetration testing results with business intelligence (BI) tools such as Power BI or Tableau can greatly enhance reporting capabilities. These tools enable organizations to visualize data effectively and generate comprehensive reports on security assessments.
Benefits of Using BI Tools
Enhanced Visualization
BI tools allow for dynamic reporting, making it easier for stakeholders to understand complex security data. By presenting findings in a visually appealing manner, organizations can facilitate better communication about security issues.
Integration with Existing Systems
Many BI tools can easily integrate with existing security frameworks, streamlining the reporting process. This integration enables organizations to create dashboards that display real-time data from penetration tests and other security assessments.
How to Choose the Best Penetration Testing Option
Selecting the most suitable penetration testing method involves considering various factors, including the organization’s needs, team size, budget, and risk levels.
Assess Organizational Needs
Determine what specific vulnerabilities you want to address, whether they are related to web applications, networks, or systems. Understanding the organization’s unique security landscape is crucial for effective testing.
Team Size and Expertise
Evaluate the skills and capacity of your internal team. If they lack experience, consider outsourcing or using automated tools. Organizations with larger teams may find it beneficial to conduct more comprehensive testing in-house.
Budget Considerations
Understand your budget constraints. While outsourcing can be costly, investing in comprehensive penetration testing can save money in the long run by preventing security breaches. Balancing cost with quality is essential for effective security measures.
Risk Level
Consider the potential impact of security breaches on your organization. Higher risk levels may necessitate more frequent and comprehensive testing. Organizations in highly regulated industries may face greater scrutiny and need to prioritize security testing accordingly.
Best Practices for Penetration Testing
To ensure the effectiveness of penetration testing efforts, organizations should adhere to best practices:
Regular Testing
Conduct penetration tests on a regular basis to keep up with evolving threats. This is particularly important as new vulnerabilities are discovered and systems are updated.
Comprehensive Scoping
Clearly define the scope of each penetration test. This includes specifying which systems, applications, or networks will be tested, as well as any limitations on testing methods.
Post-Testing Review
After conducting a penetration test, review the findings with relevant stakeholders. Develop a plan for remediation based on the identified vulnerabilities and ensure that lessons learned are applied to future testing.
Continuous Improvement
Utilize feedback from penetration tests to enhance security policies and practices. Continuous improvement helps organizations stay ahead of emerging threats and strengthens their overall security posture.
Conclusion
Penetration testing is a critical element of an effective cybersecurity strategy. By understanding the different types of testing, available tools, and best practices, organizations can better protect their sensitive data and systems from cyber threats. Whether opting for external penetration testing services, leveraging automated tools, or using professional BI tools for reporting, the key is to remain proactive in identifying and addressing vulnerabilities. As cyber threats continue to evolve, so too must our approaches to securing our digital assets.