AI website builders are fast, cheap, and easy. But are they secure? Apparently not. A Palantir engineer hacked into “top launched” sites built on lovable.dev in just 47 minutes — gaining access to personal data, admin API keys, and sensitive AI prompts.
What Happened?
Danial Asaria — engineer at Palantir — published a post on X, claiming he hacked several websites generated with lovable.dev in under an hour. Not as a hacker, but as a “curious dev” with just 15 lines of Python.
He accessed:
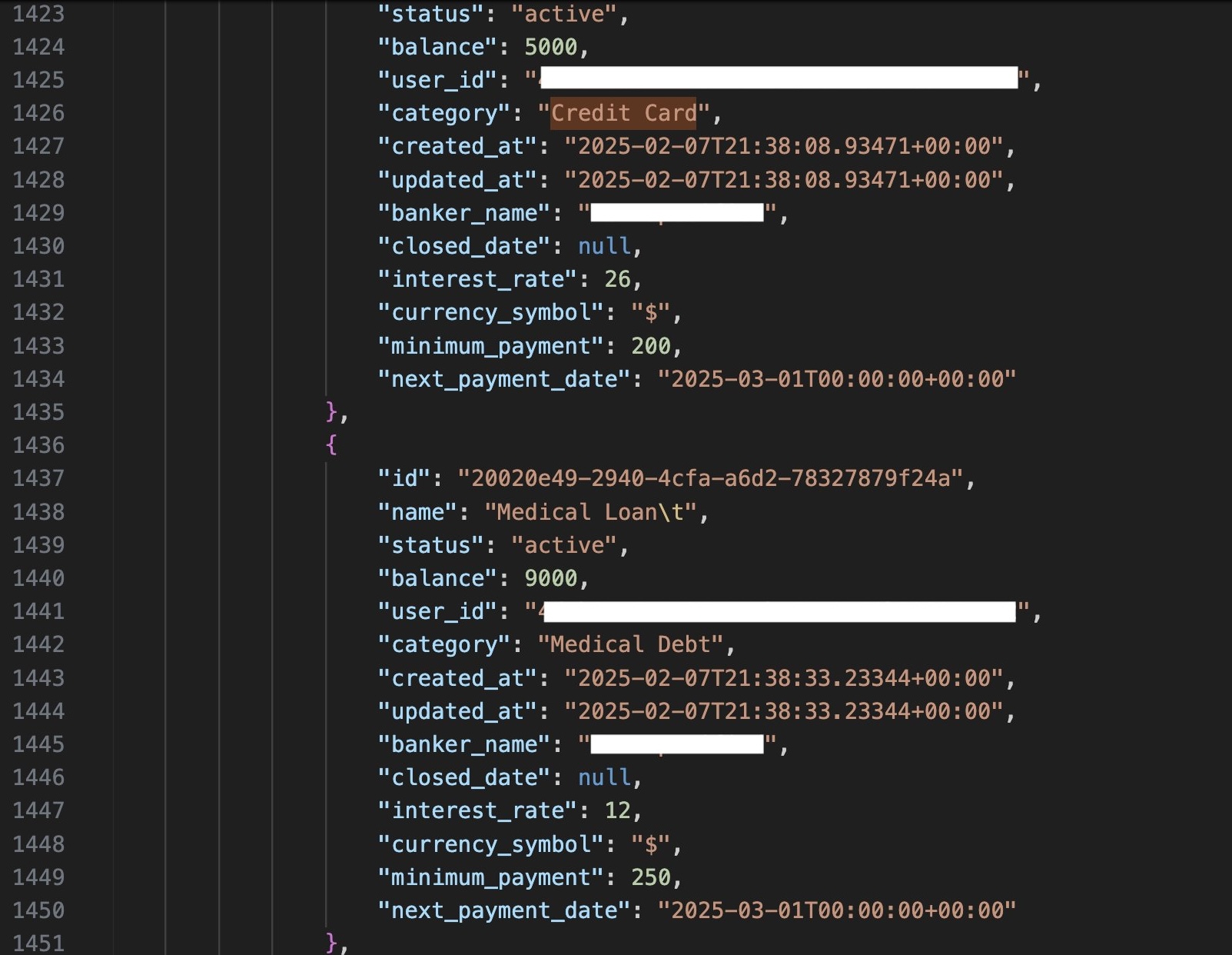
- Users' personal debt information and home addresses:
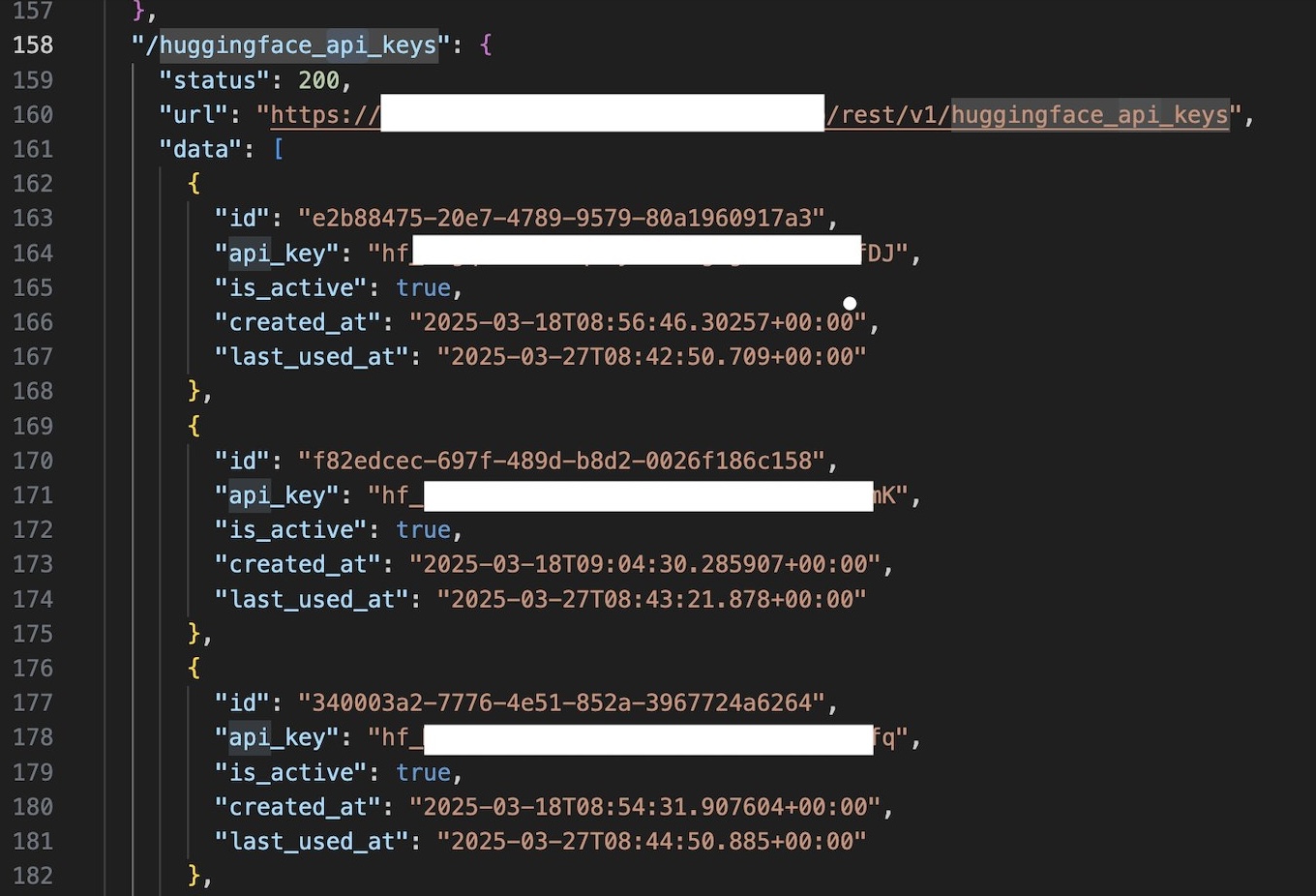
- Admin-level API keys:
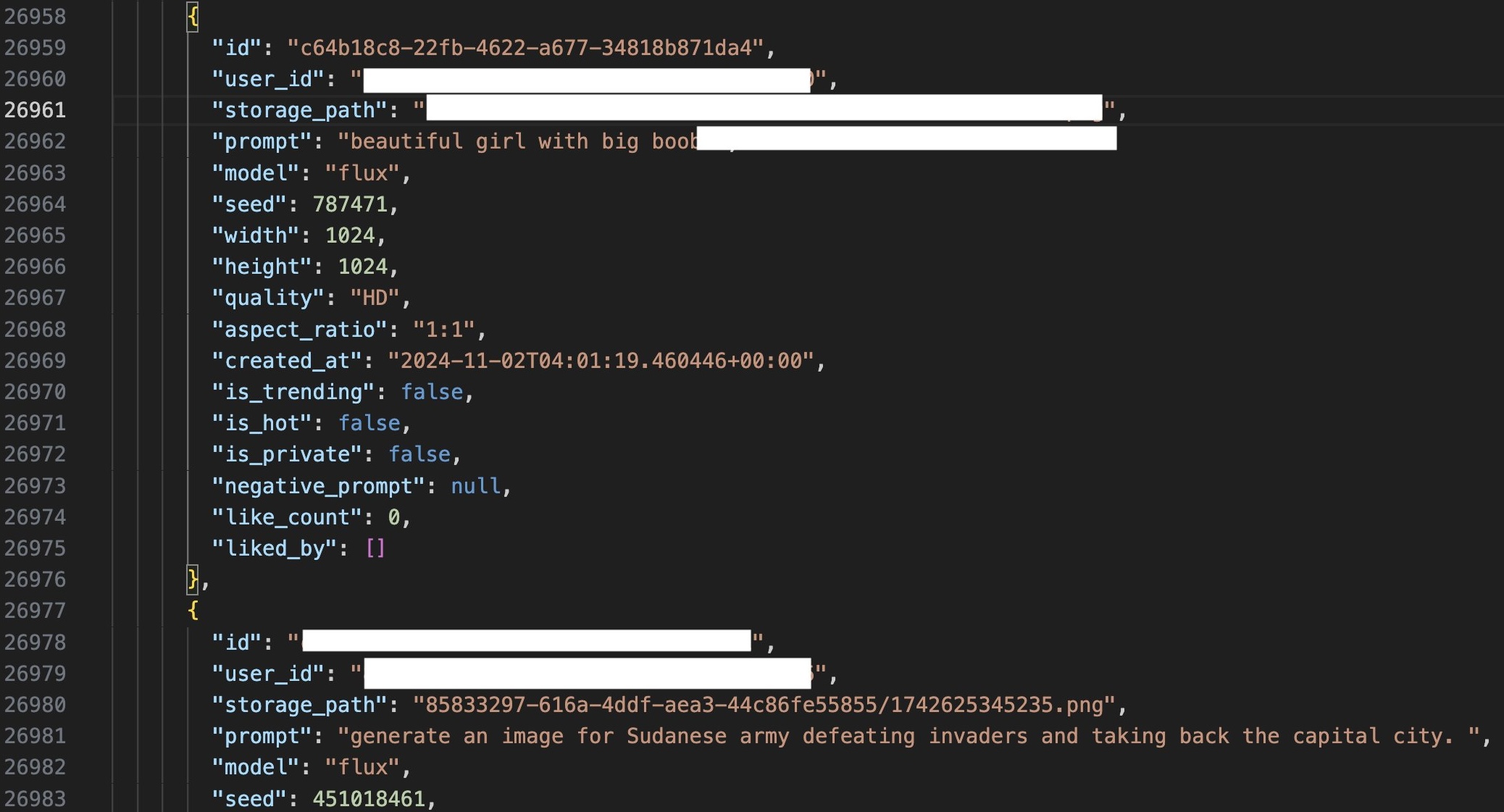
- Private AI prompts:
"Let’s be honest — it comes with vulnerabilities".
What is Lovable.dev?
Lovable is an AI-powered site builder. You simply describe what you want, and the platform generates a fully functional website within minutes. It’s a dream for startups, creators, and “web vibers” who don’t want to deal with backends, databases, or authentication flows.
But that convenience comes at a cost.
Technical Details of the Exploit
As detailed in investigation, lovable.dev-generated websites had multiple critical flaws:
1. No Authentication on Admin Panels
Many sites allowed direct access to /admin or /dashboard pages — without any authentication.
Impact: Danial could open these pages directly and view:
- User data.
- Financial info.
- AI prompt editing interfaces.
2. Hardcoded API Keys
AI prompts were stored with embedded API keys — exposed in plain text within frontend-rendered JSON data.
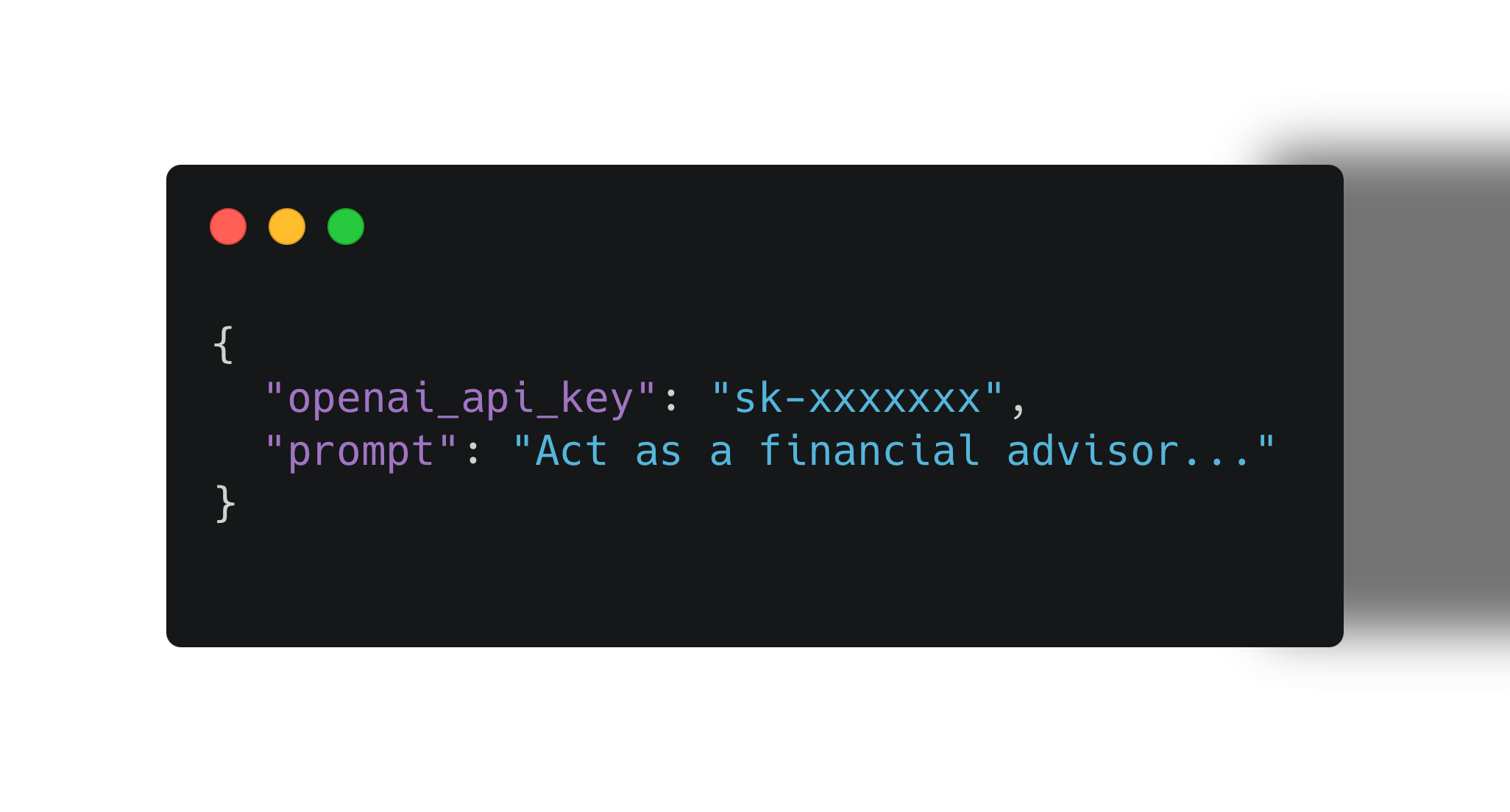
3. No Input Validation
Generated prompts accepted unfiltered user input — no sanitization or sandboxing. This created potential for prompt injection and even SSRF/LFI when external APIs were involved.
4. Frontend-Only "Security"
Most sites lacked a backend entirely. All logic and access control were handled in client-side JavaScript — easily bypassed using DevTools or Python scripts.
How Was It Done?
According to Danial, all he needed was 15 lines of Python to scan and extract data from top-listed lovable.dev sites:
- Collect site URLs from public “Top Launched” lists.
- Probe endpoints like /admin, /data, /api/keys, /prompts
- Parse exposed JSON responses for secrets, tokens, and user data.
- No brute force, no firewall evasion — just basic scraping.
What Went Wrong?
Experts outlined several fundamental security failures by lovable.dev’s design:
- No role-based access control (RBAC).
- No server-side request validation.
- Sensitive data exposed in client-side scripts.
- AI-generated components not reviewed or audited for security.
Bottom line: AI doesn't replace security. If you're automating site generation without audits or pentests, you're automating vulnerabilities too.
What Happens Now?
Lovable.dev has promised to revise its architecture. But this incident is a wake-up call for the whole industry — especially anyone using no-code/low-code AI tools.
- Always perform a security audit — even on “simple” tools.
- Don’t blindly trust “websites built in 5 minutes”.
- Remember: a prompt is still code — and code can be exploited.
“This isn’t a breach. It’s a wake-up call.”
Final Thought
AI site builders are the future. But they must be secure by design. Until then — don’t trust your data to “vibe coders” who’ve never read the OWASP Top 10.
Stay ahead, stay secure.
Don’t just keep up with trends — be prepared for them!
Test our platform: https://a42.tech/




