Artificial Intelligence (AI) has been a game changer across industries, from healthcare to finance. However, the same technology empowering businesses is now being weaponized by cybercriminals. Enter GhostGPT, a shadowy AI tool reportedly making waves in the underground hacking community.
What Is GhostGPT?
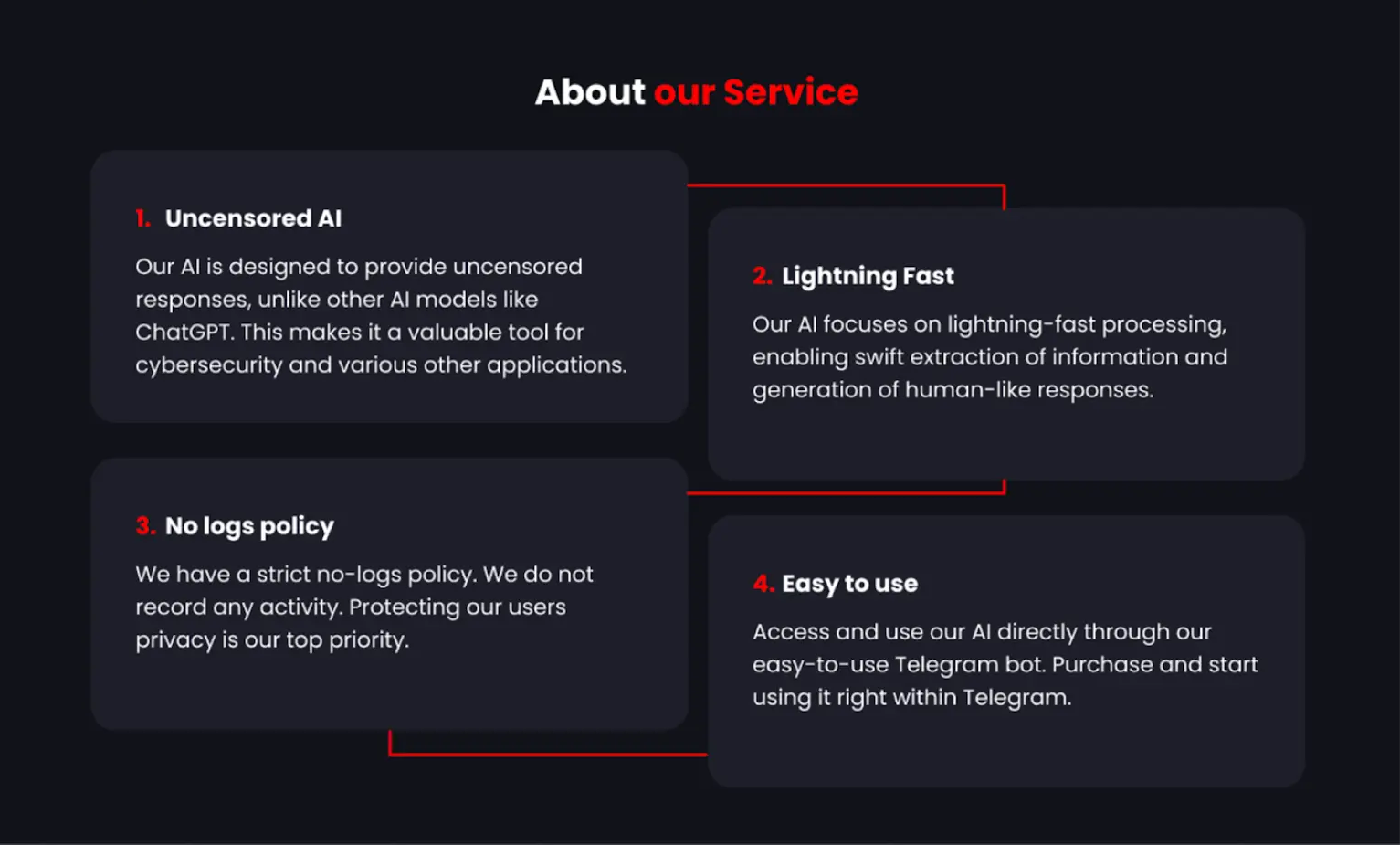
GhostGPT is a custom-built generative AI tailored for malicious purposes. While tools like ChatGPT are trained with safeguards to prevent misuse, GhostGPT appears to have stripped-down ethical filters, making it an enabler for illegal activities. Hackers leverage it to automate complex tasks, including creating convincing phishing campaigns, generating malware code, and even bypassing common cybersecurity protocols.
How Cybercriminals Are Using GhostGPT
Unlike conventional hacking tools, GhostGPT brings a new layer of sophistication:
1. Phishing Campaigns at Scale.
GhostGPT can craft emails that mimic legitimate organizations, complete with personalized details, to fool victims. It goes beyond basic templates, adapting tone and style to match the target’s behavior.
2. Advanced Malware Development.
It accelerates malware creation, generating obfuscated code that is harder for antivirus tools to detect. Hackers can also use it to find vulnerabilities in applications and design custom exploits.
3. Social Engineering and Reconnaissance.
By analyzing publicly available information about a target, GhostGPT can suggest tailored social engineering scripts, making attacks more convincing.
The Implications for Cybersecurity
GhostGPT represents a significant shift in cybercrime, making advanced hacking tools more accessible than ever. By offering its services through platforms like Telegram, it removes the need for technical expertise, allowing novice attackers to participate in cybercrime with minimal effort. This convenience has lowered the barrier to entry, enabling a broader range of individuals to create phishing emails, malware, and other malicious content with remarkable ease.
Moreover, GhostGPT enhances the efficiency of experienced attackers by streamlining tasks like malware refinement and phishing campaign creation. Since users can simply pay a fee to gain immediate access to this AI tool, they can focus entirely on executing their attacks without needing to set up complex systems or jailbreak legitimate AI models.
The popularity of GhostGPT, evident from its widespread mentions on cybercrime forums, indicates a growing trend in the use of AI tools for malicious purposes. This highlights an urgent need for AI-driven defensive measures, as traditional cybersecurity solutions often struggle to detect the highly sophisticated outputs generated by such tools.
Countermeasures: Fighting AI With AI
Cybersecurity companies and researchers are already leveraging AI to identify and neutralize threats like GhostGPT:
1. AI-Driven Threat Detection.
Advanced AI systems are being trained to detect anomalies in network behavior and identify malicious code patterns generated by GhostGPT-like tools.
2. Collaborative Intelligence.
Organizations are pooling resources through threat intelligence platforms to share insights on emerging AI-driven threats.
3. Policy and Regulation.
Governments and industry leaders are discussing stricter regulations on AI development and access, aiming to limit the misuse of such technology.
Final Thoughts
The emergence of GhostGPT raises critical questions about the future of cybersecurity. It blurs the line between skilled and novice hackers, as even individuals with minimal technical knowledge can execute advanced attacks with AI’s assistance.
More worryingly, GhostGPT’s ability to learn and adapt could make it a challenge for traditional security measures to keep pace. For instance, malware generated by GhostGPT could use polymorphism—changing its structure dynamically—to evade detection.
To combat this rising threat, it is recommended that organizations invest in AI-driven security solutions capable of detecting and neutralizing sophisticated attacks. Additionally, fostering collaboration through threat intelligence sharing and adopting a multi-layered defense strategy can significantly enhance resilience against AI-powered cybercrime.
Don’t just keep up with trends—be prepared for them!
Test our platform: https://a42.tech/