In February 2025, cybersecurity researchers uncovered a large-scale campaign where over 10,000 compromised WordPress sites were used to distribute malware targeting both macOS and Windows systems. This attack highlights the critical need for regular updates and security monitoring, particularly for websites running on open-source platforms like WordPress.
Technical Details of the Attack
Attackers exploited vulnerabilities in outdated versions of WordPress (e.g., 6.7.1) and its plugins to inject malicious code into legitimate websites. These vulnerabilities included unpatched security flaws in themes, plugins, and misconfigured site permissions, allowing attackers to gain unauthorized access and modify website content.
The primary infection method involved injecting malicious JavaScript via the <iframe> HTML element, which enables embedding one webpage within another. This technique allowed attackers to discreetly load harmful scripts without user interaction, making detection more challenging.
Once executed, the malicious JavaScript performed the following key functions:
1. Dynamic Content Injection: The script dynamically generated fake browser update prompts based on the user’s operating system and browser type.
2. Obfuscation and Anti-Analysis Measures: The injected scripts were heavily obfuscated using encoding techniques, such as Base64 encoding and hexadecimal representation, to evade detection by security tools and analysts.
3. Multi-Stage Redirection: Users visiting compromised websites were automatically redirected through multiple intermediary domains. These domains acted as traffic distribution systems (TDS), filtering visitors based on geolocation, user-agent strings, and other characteristics to determine the appropriate payload.
4. Conditional Execution: The malware payload was only delivered if specific conditions were met, such as:
- Checking the user-agent string to determine the operating system (Windows or macOS).
- Verifying the IP address and geolocation to avoid security researchers and sandboxes.
- Ensuring the user was visiting from a non-virtualized environment, using fingerprinting techniques to detect virtual machines and automated analysis tools.
Malware Distribution for macOS and Windows
A distinctive characteristic of this campaign was its ability to deliver tailored malware payloads depending on the victim’s operating system. This technique allowed the attackers to exploit the unique vulnerabilities associated with each platform, thereby maximizing the attack's reach.
Windows Payload - SocGholish
For Windows users, the attackers deployed a variant of the SocGholish malware, a well-known strain that masquerades as a legitimate browser update. Once the victim downloaded and executed the malicious payload, the malware gained persistence by injecting itself into the system’s memory. This enabled remote access to the compromised system, allowing the attackers to execute arbitrary commands, upload additional malware, and exfiltrate sensitive data.
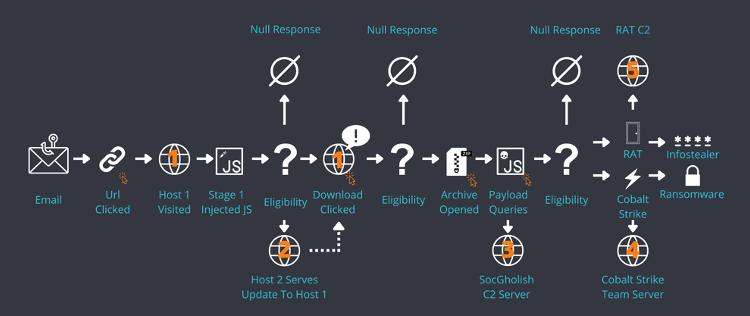
1. Execution Method.
SocGholish often leverages social engineering tactics to convince users to download the fake browser update. The payload is typically delivered through drive-by-downloads or phishing links embedded in compromised WordPress sites.
2. Functionality.
Once activated, SocGholish communicates with a remote Command and Control (C2) server to download additional modules or tools. These modules may include keyloggers, remote administration tools (RATs), or credential stealers, depending on the attacker’s objectives.
3. Evasion Techniques.
To evade detection, SocGholish utilizes various anti-analysis mechanisms, such as obfuscating its code and utilizing encrypted communication channels for C2 communication. It may also disable Windows Defender and other security software to maintain stealth.
macOS Payload - AMOS (Atomic macOS Stealer)
For macOS users, the attackers deployed AMOS, a sophisticated malware strain specifically designed to target macOS systems. AMOS operates as a stealer, collecting a wide range of sensitive data from the victim’s system, including saved passwords, browser history, SSH keys, and even cryptocurrency wallet credentials.
1. Execution Method.
AMOS is typically delivered via a malicious disk image (.dmg) file, which is often disguised as a legitimate software update or a file related to a known application. When the victim opens the disk image, the malware payload is extracted and executed on the system.
2. Functionality.
Upon execution, AMOS scans the system for various data types, focusing on sensitive information stored in browsers (e.g., Chrome, Safari) and cryptocurrency wallets (e.g., Bitcoin, Ethereum). The stolen information is then exfiltrated to the attacker’s C2 server using encrypted HTTP(S) connections.
3. Evasion Techniques.
To avoid detection by macOS security features, AMOS uses code obfuscation techniques and employs memory injection to hide its presence from common security software. It also has built-in checks to determine whether the malware is running in a virtual environment or sandbox, and if so, it terminates its execution.
Mitigation and Security Recommendations
To protect against such attacks, WordPress site administrators and users should follow these best practices:
- Keep WordPress and plugins up to date: Regular updates help patch known vulnerabilities that attackers exploit.
- Use security plugins: Reliable security plugins can detect and block malicious activity before it compromises the site.
- Perform regular security audits: Conducting vulnerability assessments and penetration testing helps identify and mitigate security risks.
- Monitor for suspicious redirects: Implement tools that track unauthorized changes to website content and prevent malicious redirections.
- User education: Increasing awareness about phishing tactics and malicious downloads can reduce the risk of successful infections.
Final Thoughts
This campaign exemplifies the growing sophistication of cybercriminal operations, particularly in their ability to distribute tailored malware across different operating systems.
The use of compromised WordPress sites as an infection vector is not new, but the attackers’ refined techniques — such as obfuscated JavaScript, multi-stage redirections, and conditional payload delivery — demonstrate a high level of adaptability.
Don’t just keep up with trends — be prepared for them!
Test our platform: https://a42.tech/