In cybersecurity, even the smallest oversight can lead to significant vulnerabilities. A recent discovery about Mastercard’s DNS records is a reminder of how critical it is to maintain rigorous DNS hygiene.
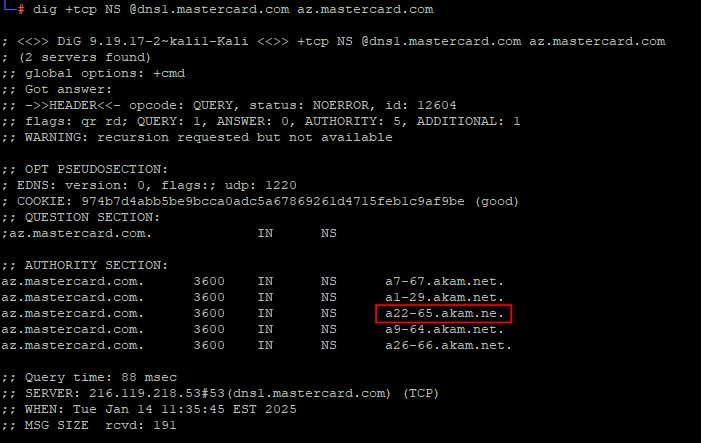
For over 4.5 years, one of Mastercard’s subdomains contained a typo in its Name Server (NS) record. Instead of pointing to a22-65.akam.net (Akamai Technologies), it incorrectly pointed to a22-65.akam.ne. This minor error introduced a serious risk of subdomain takeover, phishing, and data interception.
Why DNS Typos Are Dangerous
DNS misconfigurations like typos can open the door to numerous threats, including:
1. Subdomain Takeover.
Attackers can register the typo domain and gain control over traffic intended for the original domain.
2. Phishing and Data Theft.
Threat actors may exploit the situation to intercept sensitive data or launch phishing campaigns.
3. Man-in-the-Middle Attacks.
Misconfigured DNS records can facilitate traffic rerouting through attacker-controlled servers.
This particular case became even more alarming when reports revealed that the typoed domain had been registered by an individual in Russia in 2016 and intermittently resolved to a German IP address (185.53.177.31) for several years.
In this case, Mastercard initially ignored the vulnerability disclosure and dismissed the risk publicly. However, the reality is that DNS misconfigurations can have cascading effects. For instance, 76 other Mastercard domains were linked to a single insecure IPv4 address, compounding the potential for exploitation. This lack of accountability not only exposes organizations to significant risks but also increases costs that are often passed down to consumers and taxpayers.
What You Can Do
1. Audit Your DNS Records. Periodically check records for typos, misconfigurations, or inactive entries.
2. Monitor Subdomains. Ensure all subdomains are properly secured and not vulnerable to takeover.
3. Use a Comprehensive Security Tool. Platforms like A42.tech provide automated scanning and monitoring to detect vulnerabilities such as DNS misconfigurations and subdomain takeovers in real time.
How A42.tech Protects Against DNS Vulnerabilities
At A42.tech, we take DNS security seriously. Our tools include features specifically designed to identify and mitigate risks like subdomain takeovers and DNS misconfigurations. By leveraging automated, continuous scanning, we help businesses safeguard their digital assets and prevent similar incidents before they occur.
Final Thoughts
The Mastercard incident is a cautionary tale of how a seemingly small oversight can escalate into a major security vulnerability. Don’t let this happen to your organization. Take proactive steps to secure your DNS records and protect your brand, your customers, and your reputation.
Don’t wait for vulnerabilities to compromise your business.
Visit the A42.tech today and start scanning your infrastructure for potential risks: https://a42.tech/
Stay secure, stay ahead.




