When organizations undergo vulnerability assessments or penetration testing, many assume the SOC (Security Operations Center) team has full visibility and a crystal-clear view of everything that’s happening. In reality, however, the view from within a SOC often resembles a black box. This article explores what is actually visible to SOC analysts during such engagements, what remains hidden, and how that limited visibility shapes an organization’s security posture.
The Illusion of Total Visibility
Security logs, alerts, and telemetry may appear comprehensive, but in practice, they are often fragmented across multiple systems - including endpoint detection and response (EDR), firewall logs, DNS logs, SIEM platforms, and cloud telemetry. During a vulnerability assessment or red team exercise, analysts rely heavily on correlation rules and behavioral baselines to detect anomalies. Yet without sufficient context, even a high-fidelity alert may amount to nothing more than a dot on a map.
What SOC analysts typically observe:
- New or unexpected external IP addresses interacting with internal services.
- Reconnaissance behavior such as port scanning, SMB enumeration, and unusual LDAP queries.
- Credential anomalies, including NTLMv1 usage, Kerberoasting attempts, or lateral movement via tools like PsExec and WMI.
- Custom or obfuscated PowerShell scripts, Cobalt Strike beacons, or abuse of legitimate system binaries (LOLBins) etc.
- Fileless malware or suspicious persistence mechanisms, such as registry modifications or malicious scheduled tasks.
What remains hidden from SOC view:
- The intent behind observed actions - e.g., whether activity is part of a red team exercise or a genuine intrusion.
- The vulnerability status of target systems, unless explicitly flagged by scanning tools.
- Malicious activity that blends in with legitimate behavior, such as logins using stolen credentials from known IP addresses during typical working hours.
- Visibility gaps resulting from BYOD devices, unmonitored SaaS platforms, or legacy infrastructure with inadequate logging.
Detection ≠ Understanding
A common misconception is that detection automatically equates to mitigation. In practice, SOC analysts are not patch managers or infrastructure administrators. When a scanner probes a vulnerable service, it may trigger an IDS alert - but without pre-coordination or comprehensive EDR visibility, it’s often unclear whether an alert is part of a test or an actual compromise attempt.
In the absence of real-time collaboration with penetration testers or vulnerability assessment teams, many alerts enter the triage queue, sometimes days after the activity occurred. Such delays can significantly hinder effective response.
Example: A vulnerability scanner runs during a scheduled assessment and triggers an IDS alert on an outdated service.The SOC sees the alert—but without context, they don’t know if it’s a real threat or part of the test.
It’s queued and reviewed later.
No action is taken.
No configuration is updated.
The alert fades into the noise.
Takeaway: You’re testing the infrastructure, not the SOC. Without coordination, detections don’t lead to improvements.
The Power of Context in Vulnerability Testing
To maximize the value of a vulnerability assessment, organizations should ensure that their SOC or MDR (Managed Detection and Response) teams are included in the planning process. Even minimal coordination - such as defining a testing window or sharing a list of target assets - can offer significant advantages:
- Adjusting alert thresholds to reduce noise and avoid alert fatigue.
- Validating whether detection and correlation rules perform as intended.
- Observing attacker TTPs (tactics, techniques, and procedures) in a live environment.
- Enhancing detection logic to prepare for future threats.
Without such context, the SOC operates in the dark, attempting to defend against activity it wasn’t told to expect.
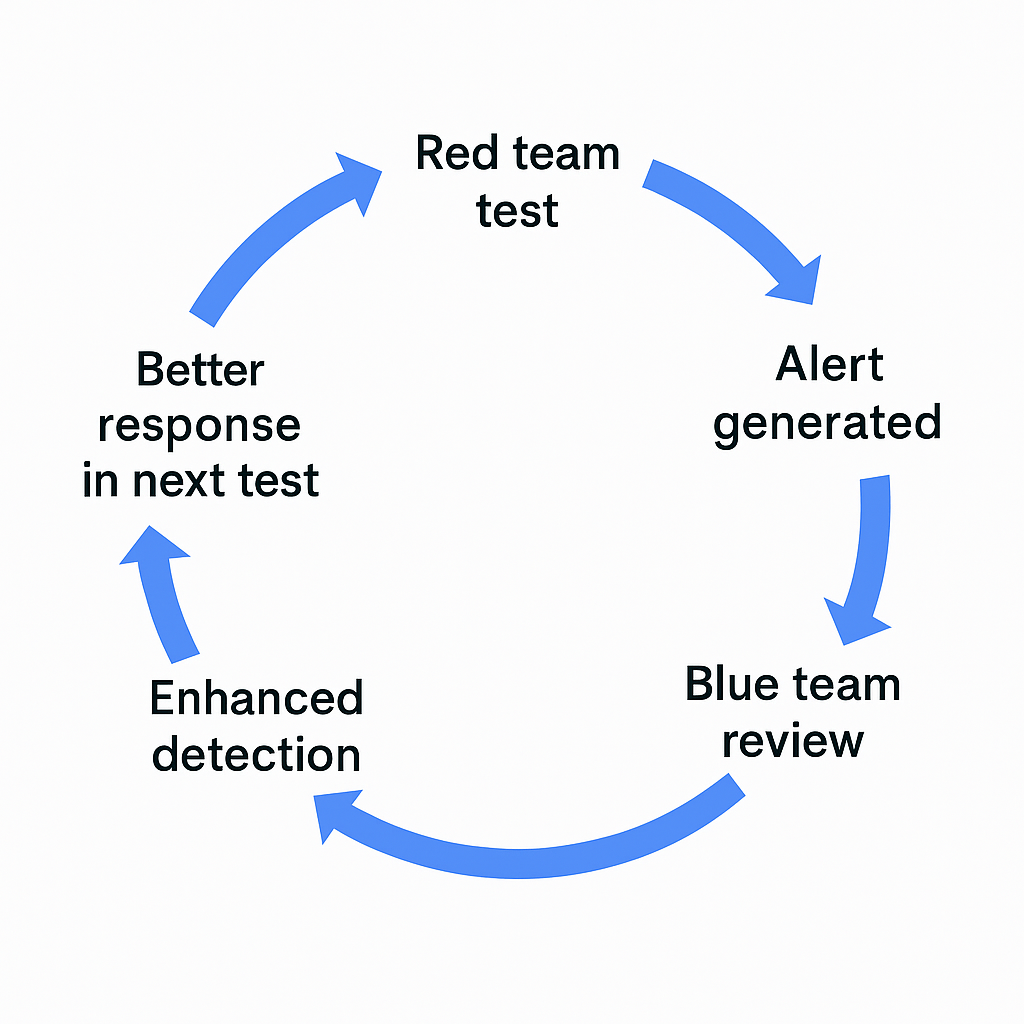
Turning the Black Box into a Feedback Loop
High-quality vulnerability assessments do more than identify system-level flaws. They illuminate visibility gaps across the organization’s detection infrastructure. A well-established feedback loop between red and blue teams leads to:
- Improved correlation rules within the SIEM.
- Refined policies and configurations for endpoint protection tools.
- More actionable threat intelligence.
- Reduced Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Final Thoughts
From the SOC’s perspective, testing activities can often resemble background noise - signal without meaning - unless the necessary context is provided. Vulnerability testing is not merely a matter of firewall rules or antivirus signatures; it’s a test of people, processes, and preparedness.
Organizations seeking to gain the most from testing initiatives should bring their detection and response teams into the loop as early as possible. The black box only stays dark if no one shines a light into it.
For teams seeking more advanced protection, the a42.tech platform delivers comprehensive vulnerability assessments, automated scanning, and SOC-integrated detection workflows - providing both offensive and defensive teams with the visibility they need to stay ahead of evolving threats.
Test smarter. Detect faster. Stay ahead.
Don’t just keep up with trends — be prepared for them!
Test our platform: https://a42.tech/