Cybersecurity vulnerabilities, such as web security misconfigurations and unpatched applications, pose significant risks that can lead to severe business disruptions or even shutdowns.
Web Security Misconfigurations
Misconfigurations occur when security settings are improperly implemented or left at default, creating exploitable weaknesses. For instance, a healthcare management platform with an enabled PUT HTTP method and lacking Cross-Site Scripting (XSS) protection allowed attackers to inject malicious code into the system’s index.html file. This breach compromised sensitive user data and disrupted operations, highlighting how such oversights can have catastrophic consequences.
Unpatched Applications
Failing to apply security patches leaves systems vulnerable to exploitation. Unpatched applications can lead to unauthorized access, data breaches, and operational downtime. For example, a financial institution running outdated software faced unauthorized access to sensitive data due to an unpatched vulnerability. Implementing virtual patching can provide immediate protection by mitigating vulnerabilities until permanent fixes are applied, thereby reducing the risk of exploitation.
Business Impact
Both misconfigurations and unpatched software can result in:
- Data Breaches: Exposure of sensitive information, leading to legal and reputational damage.
- Operational Disruption: System outages affecting business continuity and customer trust.
- Financial Losses: Costs associated with breach mitigation, fines, and loss of business.
Preventive Measures:
- Regular Audits: Conduct routine security assessments to identify and rectify misconfigurations.
- Timely Patching: Apply security updates promptly to address known vulnerabilities.
- Virtual Patching: Use virtual patching solutions to protect systems when immediate patching isn’t feasible.
And if you think that this is all about some rare cases anywhere but not in your company, well, the world trends are saying that it is not. Security misconfigurations and unpatched software are significant contributors to cybersecurity incidents. According to SOCRadar Research, security misconfigurations have caused 35% of all-time cyber incidents. [Socradar]
Additionally, the Ponemon Institute’s 2019 Vulnerability Survey found that 60% of breach victims were compromised due to an unpatched known vulnerability where the patch was not applied. Besides that, In contrast to the 8,051 vulnerabilities published in Q1 of 2022, a significant increase was observed in 2023. 26,447 vulnerabilities were disclosed, surpassing the previous year’s count by over 1,500 CVEs. This marks a continuous upward trend in the discovery of vulnerabilities year after year. [Comparitech]
Are you feeling this trend? It looks like the general situation won’t improve anytime soon. The most common vulnerabilities are still here and gaining strength. Accotding to Edgscan 2024 Vulnerability Statistics Report:
SQL Injection:
- - Persisting as the most critical web application vulnerability since 2022.
- - Remains a primary threat vector due to its severity and exploitability.
Cross-Site Scripting (Stored):
- - Ranked as the second most prevalent High/Critical vulnerability in 2023.
- - Constituted 10.5% of all high-severity vulnerabilities.
- - Requires significant effort to remediate, averaging 100 man-days per case.
Malicious File Upload:
- - Third most common High/Critical vulnerability in 2023.
- - Accounted for 7.25% of such vulnerabilities.
- - Demonstrated an even higher remediation effort, averaging 117 man-days.
Here some additional illustration of global trends from the Check Point Cyber Security Report 2022 (By the way, I highly recommend reading it — it’s quite insightful.):
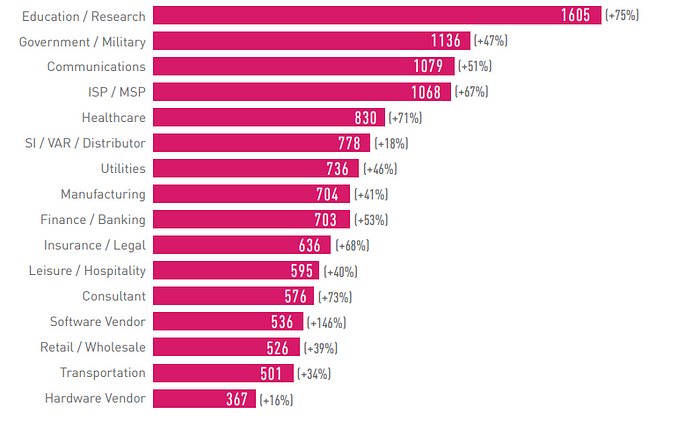
Figure 6: Average weekly attacks per organization by Industry 2021, compared to 2020

Figure 34: Percentage of attacks leveraging vulnerabilities by Disclosure Year in 2021.
As we see on Figure 34, many vulnerabilities discovered in 2017 maintained a strong presence throughout 2021. This is mostly due to popular flaws like the Apache Struts2 Remote Code Execution (CVE-2017–5638), which is incorporated into the Mirai botnet, or the PHPUnit remote code execution (CVE-2017–9841), often used to exploit vulnerable WordPress plugins.
The 2020 vulnerabilities remained prominent, leveraged in 11% of attacks. Among the most significant was the Draytek Vigor series buffer overflow vulnerabilities (CVE-2020–10826, CVE-2020–10827, CVE-2020–10828), which had a 41% share of global impact on organizations. These vulnerabilities could be leveraged to run arbitrary code on vulnerable Draytek routers, using a specially crafted remote HTTP request.
So here we see that most of the known vulnerabilities have been exploited for years! And every year, a new batch of vulnerabilities emerges. Of course, it takes time to incorporate them into attack vectors, but once they are, they can be used for many years, causing businesses significant pain and losses.
These trends underscore the persistent and evolving nature of high-severity vulnerabilities, emphasizing the need for proactive testing and robust remediation strategies to secure web applications effectively. And that’s clear that situation continue to develop in a least pleasent way. Despite having many technologies created to resolve such problems, we still see a constant rise in the number and severity of cybersecurity incidents. Either hackers have become much smarter than cybersecurity specialists (who are under constant pressure to obtain yet another certification to secure and maintain their positions in businesses), or companies don’t truly care about their security, hoping they won’t be targeted for whatever reason. In the end, it’s all about the ‘human factor.’
Proactively managing security configurations and maintaining up-to-date applications are essential to safeguarding businesses against cyber threats that could lead to severe operational and financial consequences.
Don’t wait for vulnerabilities to disrupt your business. Partner with A42 to stay one step ahead of cyber threats. Let’s work together to ensure your systems are secure, resilient, and prepared for the challenges of today’s cybersecurity landscape.